Remember the ad hoc network?
In today’s video Ferney Muñoz takes a deeper look at the Apple Wireless Direct Link and the impact it has on your wireless LAN designs.
AWDL with Ferney Munoz Transcript:
Remember those networks we used to create without an access point, the ad hoc networks?
Well let’s talk about Apple Wireless Direct Link
Hello Ferney Muñoz with Wireless LAN Professionals. Today’s question has to do with Apple Wireless Direct Link What is the impact of AWDL in our WiFi network.
Well to understand how Apple Wireless Direct Link works we have to remind ourselves about those networks that we used to create back in the day without an access point. Where we had just have a device create its own network and started beaconing and other devices join. It is operated in its own way. It had advantages but lot of disadvantages.
Well Apple Wireless Direct Link is Apple’s own Apple to Apple communication protocol.
There is a group of guys, Milan, David, and Matthias they wrote a document and did some research. It’s called One Billion Apple’s Secret Sauce has to do with AWDL.
So I did some research to answer today’s question and yes let’s talk about AWDL.
This protocol is created by Apple devices. You know when you are transferring a file using airplay, or the way you communicate to your Apple TV, or you watch your iPad talking to your iPhone, or when you are configuring a new iPhone and your iPhone comes up brand new and says, “Oh, I want to transfer all the files from another iPhone”. It searches whatever iPhone is nearby and then it starts transferring all the files All these Apple to Apple communications happen riding on AWDL.
So how does this work?
Well devices will create this network. Let’s start with a packet capture and let’s see how it works. Let’s look at a sidecar. Yes sidecar without any wires attached. The computer is making the iPad a secondary screen. That’s fascinating.
Let’s look at this packet capture.
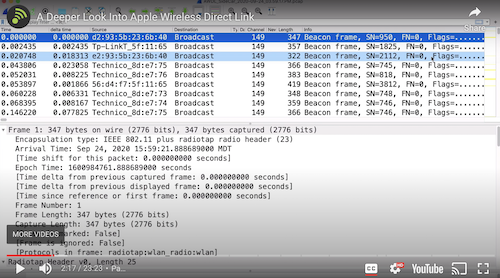
Initially, there was just regular traffic on Beacon Frame. You’re going to see request responses just the normal traffic that we see in our NIC. I captured about 250,000 frames. I color coded all of my apple wireless direct link frames with pink.
So let’s look at this master indication frame. These are the first 8 WDR of frame out of this capture that we see on top. We have the arrival time all the time stamps and the radio type header information the channel that it is using his channel using Channel 149
The signal strength it shows us also very important that this is a frame that is not going to the DS and it’s not coming from the dB So 2 DS and from DS is set to zero zero meaning this frame is going from air to air, is not touching your infrastructure.
Also there is the source and transmitter address. This is a device sending this massive indication frame and it goes to 5 and there is a backside created by Apple.
Also, we have an Apple wireless direct link action frame information. This is a massive indication frame. And looking down lower it’s going to have some availability windows and it is always said to 16 transmit units each transmit unit is 1024 microseconds. It has some the Channel Sequence that is going to be using It has the address of the master device and also a Master Metric.
The first device that creates the network is going to self assign a Master Metric and as other devices join that network they will assign a different metric based on the software version that they’re running and they may assign a lower or a higher based on who’s got the newest OS.
Also on this master indication frame it highlights which ones are the social channels that Apple is going to be using and by default it’s going to be using Channel 6, 44 and 149. These are the preferred channels for these communication protocol to operate. Also we will see all of the high throughput capabilities of 802.11 and capabilities it specifies that yes this device can use 40 megahertz channels It also specifies aggregation at the MAC data units and service data units.
All of that information is disclosed in this master indication frame. Also we can see periodic synchronization frames. These frames are similar to the master indication frame but they have less information. Both the master indication frames and the periodic synchronization frames are sent by any device and even a device that is not the master can send the master indication frame letting everybody know who the master is and what the Mac address of the master device is.
And letting everybody know that that network has been created and showing all of the election parameters and showing the channels and showing the social channels and showing all of the information for any other device that joins the wants to join the network.
Now the devices well since they are using not only their high throughput capabilities but if it is an AC device it will also disclose all of its very high throughput capabilities.
And also notice down here this version element that it will disclose if it is an IOS operating system or if it is MacOS because each device is going to be disclosing this information.
Ok so this is the first part how is the network setup. One device will create the network and other devices will join and they will start broadcasting master indication and periodic synchronization frames there will be lots of these frames being sent and enable Some of the concerns that they originally had were with the privacy security. There is no authentication I didn’t have to authenticate but it relies on upper layer security.
For instance, if you want to share a file from your computer that’s when you go to we just bring this window here it’s like if I want to share this file and I go to share and I want to use air drop the device will search for other devices nearby using iOS and right now it’s doing a discovery using Bluetooth.
And yes it found one device it found the device there is the iPad there is another MacBook Pro and if I choose one of these devices then it’s going to be establishing that communication with those devices.
Once the devices are joined and part of this domain then they will use these channels that the master has indicated and also the channel sequence and it will start transferring data.
So the security at that level depends on if you are allowing contacts only or if you are allowing everyone to send you files or if the devices have received files off it’s just not going to participate. And also if you are doing an Apple TV then you’re going to rely on the Apple TV having security and also having a passcode so that when a device wants to stream from an iPhone or an iPad or a computer into an Apple TV it’s going to have to enter that passcode that key code so that it is an authorized device to transmit.
Some of the other security issues they had was initially they had the real MAC address being displayed so they even before the randomization of MAC address that we’ve seen lately they started doing that on their devices.
For instance, if we look at some of the traffic the MAC addresses are randomized when we talk about these randomization of addresses we know that if the last character of the first octet ends in 2, 6, A or E that is a randomized Mac address.
Looking at our capturing this just look at this master indication frame the address like the infrastructure address that it has created an ea so that second character ends in a that means that that is a randomize address.
If we look at the master address yes it is also randomized.
If we look at the radio information looking at this source and destination address this source in this case random we look at any master indication 102. This is another one that is randomized and if the previous frequency notice that it’s be, the second character is an e meaning this is a random.
If I apply the filter AWDL out of the 250,000 frames that I capture we will see that it is a small percentage only 4%, about 9,000 frames were master indication and periodic synchronization frames.
That may not seem like much but I’m just talking about two devices participating in this group and all of these addresses that we see here they end in 2, ea and there must be some sixes down there but as you can see all of these are randomize MAC addresses.
Interestingly enough in the example that I did over here one of the devices an Apple TV did not randomize the MAC address. Also another concern was that devices can hijack the session and take over files or or send other files that were not intended to the recipient one of the measurements against that vulnerability is that there is a threshold of RSSI if the device is -65 or weaker then is not going to be able to participate in this network. Meaning that for you to be compromised you’re going to have to have the attacker be in close proximity of the devices that are participating on the network.
DHCP and DNS what is the impact of these services on our network?
Well Apple was aware that any overhead on our Wi-Fi network is unwanted So for DHCP these devices are not going to use any network discovery protocol or ARP so they will create their own IPv6 network using addresses starting with F F F E F D F C which are private addresses. And they will assign addresses and in a way that they are not interfering with each other.
if I applied the filter IPv6 now Wireshark is going to show me only the addresses that are sent using IPv6 and notice that it’s all of the traffic that is generated with these addresses if I click on any of those frames we can look at the source and destination MAC address.
And notice that it is using randomize MAC addresses for source and destination. We are yes using this BSS ID that is Apple and it is created for this network the purple traffic that is DHCP traffic the light blue traffic that’s UDP traffic.
Yes the protocol will use UDP or it will use TCP depending on what it’s sending.
In regards to DNS Apple will create its own dot local domain and it will create .2 records and it will create service records and txt records for the hostnames with randomize names. Although in our example we did noticed that the Apple TV had some records that were created using its real hostname it was not randomize and also on top of that even though it is supposed to create randomize addresses and hide the identity of the device this Apple TV that participated was not only the name was disclosed Clear text office apple tv but also the Mac address was revealed this is the original Mac address maybe was an older version of the Apple TV.
So one of the advantages is that Apple will use the maximum capabilities of the device and the protocol it already has a Wi-Fi chip and it uses entirely the Wi-Fi chip for this communication.
So let’s look at the capabilities some of them are the aggregation of protocol data units and service data units Let’s look at one of these notes that we have. We could see in the aggregation 2 and up to 3 max service data units aggregated also.
And we apply the filter of WLAN underscore aggregate Want to see about 16% of the traffic about 42,000 frames are aggregated frames. Apple will use the abilities of the device to its maximum and also notice that the capabilities of the device will be used wisely.
We’re using 256-QAM with two spatial streams a data rate of 780 Mb/s So it is using the maximum capabilities of the device.
Now we have seen how Apple creates its own network how IP addressing DNS are handled and that the devices will use the maximum capabilities of the chipset.
Let’s see what happens on the spectrum in these examples.
We use multiple ones One of them we transfer a big file from two devices using Airplay. We also use iPhones and iPads transferring data to an Apple TV this first example there is an incoming file this device will accept it and look at Channel 149 through 161 it is using an 80 macOS wide channel.
And yes you see the progress bar the file is being transferred and the spectrum is being heavily utilized in these 80 megahertz channel with the primary channel being Channel 149. It completes and now this spectrum shows that there’s little activity.
In the next example we’re going to see how we generate traffic with a WiFi metric it’s just RA RF in Primary Channel 149 I will initiate the file transfer it says there is a file coming I say accept and it is not coming.
As you can see, there is activity there. Nothing’s happening. I’m looking at Channel 44 Remember those social channels 149, 44 and also in 2.4 Channel 6 was listed as one of the channels you would use let’s check in 2.4 as you can see 2.4 shows little to no activity on Channel 6
We go back to 5 gig Channel 149 still shows occupied I’m going to stop the Wi-Fi metrics and immediately after the Energy Tech Threshold is not being tripped now my data is going through notice the progress of the file is being transferred I’m going to start the Wi-Fi metric again generating some RA RF and as soon as I do so the traffic on the other secondary channel will stop.
AirDrop stops and I look and see if it moves to Channel 44 nothing as soon as I stop the Wi-Fi metrics now my file has been transferred.
So as you can see in the spectrum there will also be respecting the protocol there is energy in the channel the energy the tech threshold is being tripped. So it will wait for its turn it will content and it will wait until the medium is available it will not use the other social channels it will just stay there and wait for the medium to become idle.
In this example we have transferred a video and we’re streaming from our iPad to the Apple TV Let’s see what happens to our video.
It’s going normal, normal speeds and when the traffic starts being generated then you’re going to notice in here that yes Channel 149 is being utilized and look at the quality of the video both video and audio become unstableI. paused it, it’s good I’m going to activate it again and our transmission becomes unstable the quality of the video decreases and the audio also gets affected.
Now we have looked at the transfer from the iPad to the Apple TV and he was interrupting the streaming so the quality of the video was affected the quality of the audio was affected. Let’s see what happened to the frames during that period of time.
In this example we capture about 150,000 packets and yes you can see that all of the light blue and light purple frames are aggregated frames notice that yes we have request to send in clear to send activated before each group of frames are sent and then there is a Block Ack at the end there is constant traffic going through as we are streaming from our iPad to the Apple TV. But notice that while we were generating that traffic all of these packets were being sent were being retransmitted. All of these frames highlighted in yellow are retransmissions DCP retransmissions because the frames were being damaged it didn’t go to other social channels 6 or 44 it just stayed there and waited until the medium to be clear until it finally did and the traffic just kept going so this is the impact of that.
In conclusion What does that mean for us as Wi-Fi designers?
Well we have to consider that if we have Apple devices in our network in most cases we do then perhaps Channel 149 is not going to be a good channel to have in our channel plans. The presence of Apple devices will create these Apple to Apple communications AirPlay, AirDrop and any streaming that you do like Sidecar going to the Apple TV and any Apple to Apple communications will use the Wi-Fi chipset on their devices and even though they are playing by the rules and following the 802.11 standard they will have an impact on our networks because every time they are transmitting they will be using air time and if they’re APs in Channel 149 or one of the other channels in that space then they’re going to be contending with this Apple to Apple communications. They will be using air time and they will be increasing the amount of management and control frames that we’re going to see in those areas.
As a conclusion yes it is a good, very good protocol it allows us to communicate between Apple devices without touching our infrastructure To DS and From DS will be set to 0 0 which is good doesn’t touch our APs it doesn’t use IP addresses from our DHCP server it’s not going to hit our DNS servers either all of this is maintained and contained within the Apple environment but just keep in mind that the impact that is going to have is an air time utilization.
And yes even though it is following the rules of the protocol it’s going to be using air time you’re going to be sharing the channel with these devices so if you are supporting your Apple devices maybe you’re going to have to change your network because Apple is not going to change anything to work on your network it has some social channel 6, 44 and 149
We tried this in Europe and Channel 44 was the preferred channel given the regulatory domain where you need three channels or band C channels have a restriction then it will just default to Channel 44.
We did the exact same taste test in the UK and it just didn’t work in Channel 149 or 6 it stays on Channel 44 So that’s another consideration for you.
Hopefully that answer your questions. If you have any more questions feel free to reach out to us. If you want to learn more about how Wi-Fi works join us WLANPros.com is the site we have lots of resources and other training videos in there.
Thanks for being part of the community
Ferney Muñoz

